Unauthenticated ruleset and customize login screen in Pega

In this blog article, we will see in detail about the usage of an Unauthenticated ruleset and then a working tutorial about customizing the login screen.
This tutorial is implemented using Pega 8.2 version. Please note the corresponding HTML code may vary in the previous pega versions.
We know that in Pega, rules and data instances are responsible for all type of business processing.
Business Scenario: Assume any insurance organization say AAA. Jon and Arya they both work in Sales and Service departments respectively. Both the departments use their own Pega application to interact with the customers.Now, let’s say Jon logs in the pega application and based on his profile he will be authenticated and authorized to use the Sales application. His Sales team dashboard is rendered in his user portal.
So, What happens at the backend? How does the Sales application-specific rules get picked up? Simple answer is ‘Rule-Resolution’ based on his operator profile.
Operator ID -> Access group -> Application -> rules and rulesets (ruleset stack is formed).
Sales specifc rules got picked up because his operator and access group are pointing to Sales application. All this run time rule resolution carried out because the user is successfully authenticated and knows which application specific rules to be picked out
Now I will throw a question!! How to render a screen to user before authentication?
Obviously, the screen can be the login screen 😉 because that is the screen before authentication!
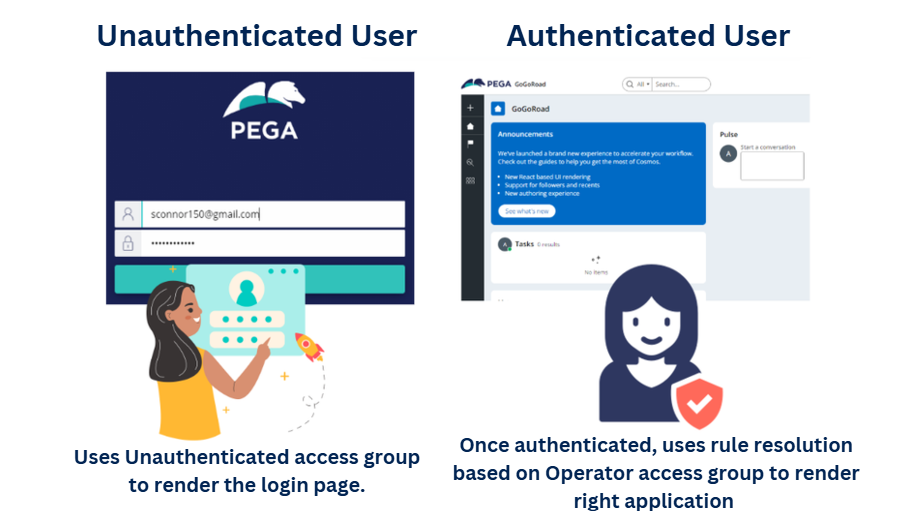
All the browser requestor sessions at the login page are usually referred as the unauthenticated or guest user sessions.
Let’s see an unauthenticated session in action!. Hit the URL
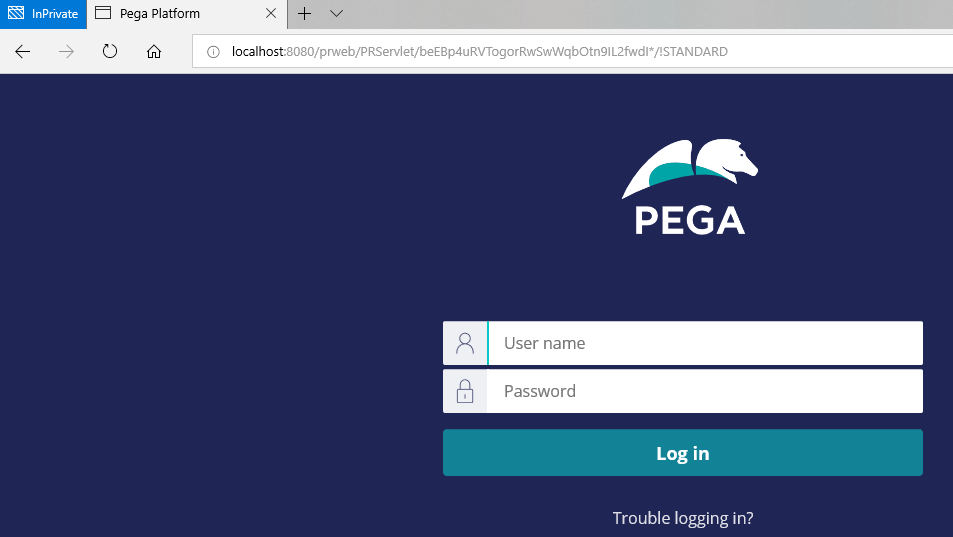
A new browser requestor session is launched and is called the unauthenticated or guest user session.
Open the browser requestor type from pega
Records -> SysAdmin -> Requestor type -> browser requestor
Open the prpc or pega Browser requestor type.
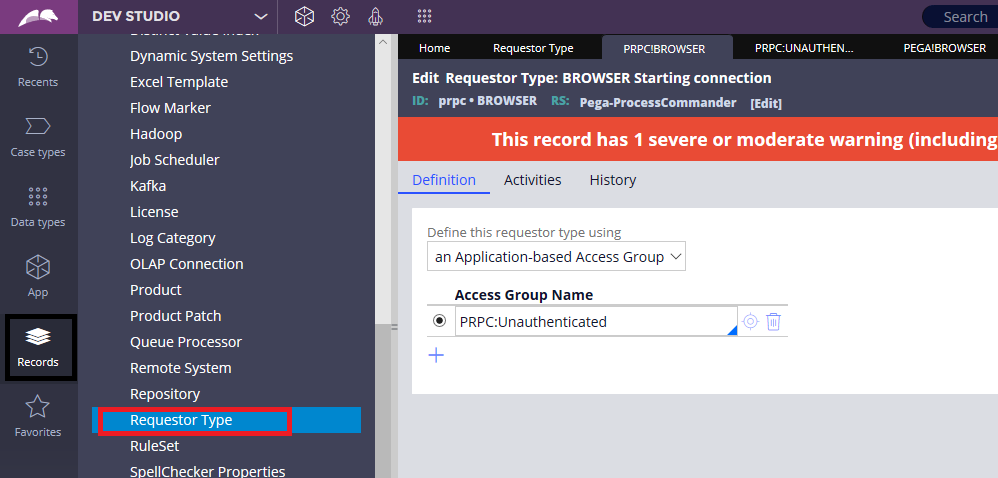
You see the requestor type references the PRPC:Unauthenticated access group.
Click and open the PRPC:Unauthenticated access group.
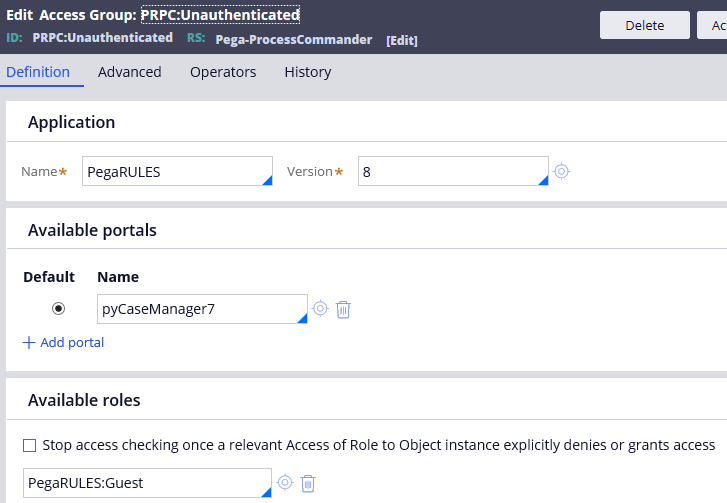
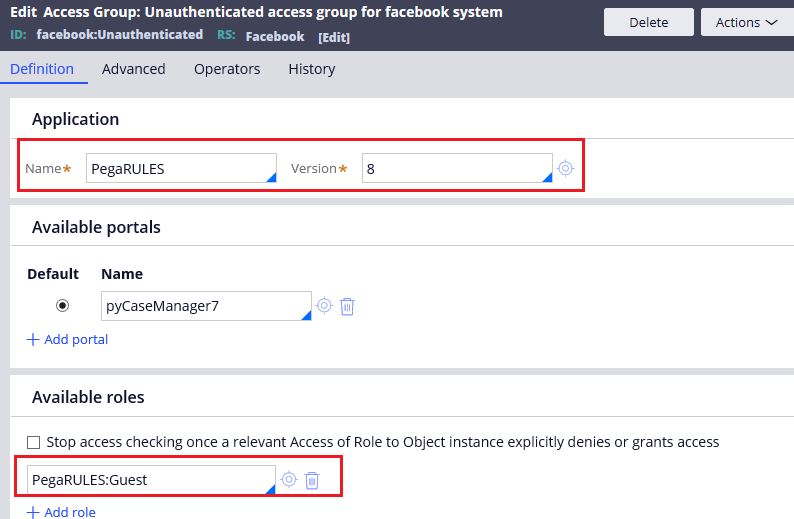
You see the application points to PegaRULES application.
It means the unauthenticated user session has access to PegaRULES application.
Now you see that the security for Unauthenticated user is well restricted to PegaRULES application alone and they don’t have any access to enterprise applications.
Let’s get back to the login screen. The HTML rule Web-Login is responsible to render the login page.
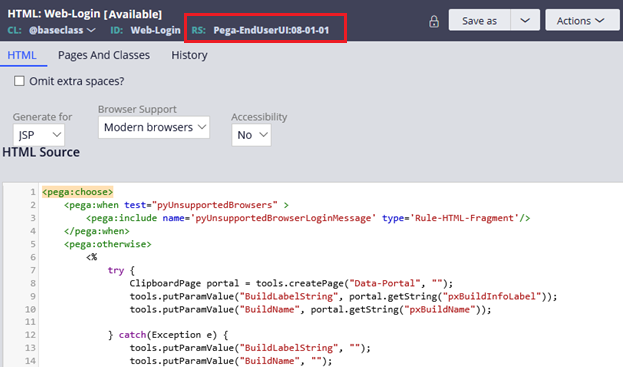
You see the rule is in Pega-EndUserUI ruleset and thus the unauthenticated users already have access to this rule under PegaRULES application.
Now think about how we can customize the Web-Login HTML rule?!
Restriction 1: The default access group prpc:Unauthenticated points to PegaRULES application. You cannot save the Web-Login HTML rule into any PegaRULES application specific rulesets.
Restriction 2: You cannot point the Unauthenticated access group to enterprise applications, because this may consider security violation by enabling the unauthenticated users access to enterprise applications.
So, there is only one solution – Create a separate unauthenticated ruleset and add it only to the Unauthenticated access group.
Let’s start the tutorial
Pre-requisite
Make sure you use your own system name.
Note: In real time, every enterprise pega projects manage their own system name.
We didn’t have a separate system name so I am going to specify a new system name
How to create a new system name?
Step 1: Create a new system name
Go to records -> System -> Create new
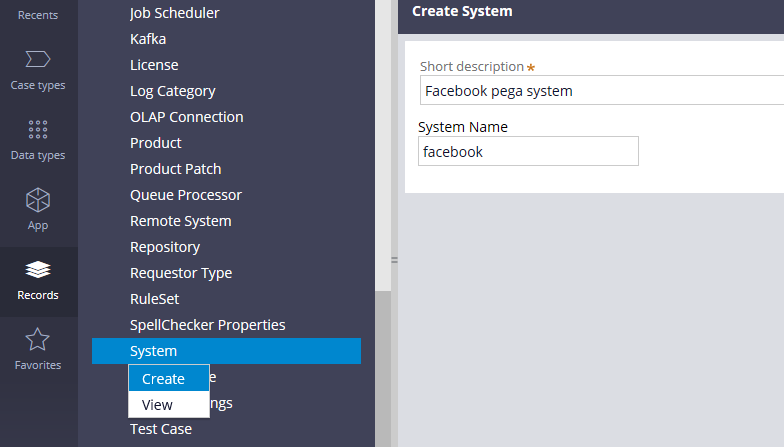
Step 2: Perform the configuration as shown below.
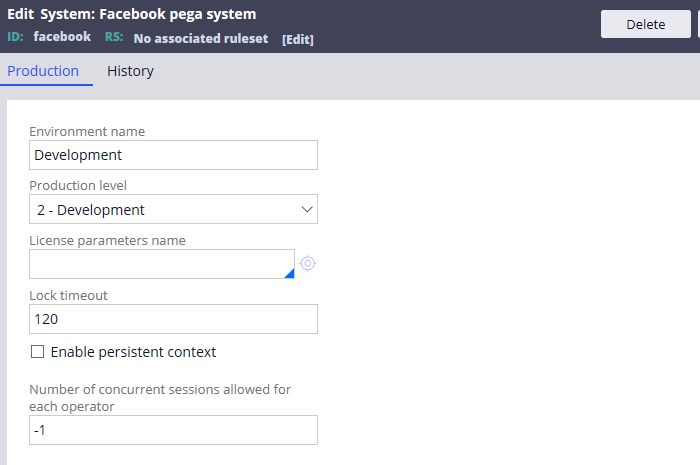
There are four main configuration fields
a) Environment name – Specify a meaningful environment name – dev ST, production etc.
b) Production level – It can range from 1-5
1- Experimental, sandbox environment
2- Development
3- Test
4- Pre-production
5- Production
c) Lock timeout – This is specific to case and not related to authentication timeout. You need to specify the timeout in minutes till which the case remains locked and after that it goes softlock. This is the system wide lock settings.
d) Number of concurrent sessions allowed for each operator – the field name explains!! You can specify the limit of pega sessions a single operator can have. Specify -1, if you need to allow unlimited sessions.
Step 3: You need to make this new system name as the default system.
This can be configured either in prconfig rule or the dynamic system settings rule (DSS). I am going to update the DSS.
Records -> SysAdmin -> Dynamic System Settings. Filter on the Setting Purpose – Identification
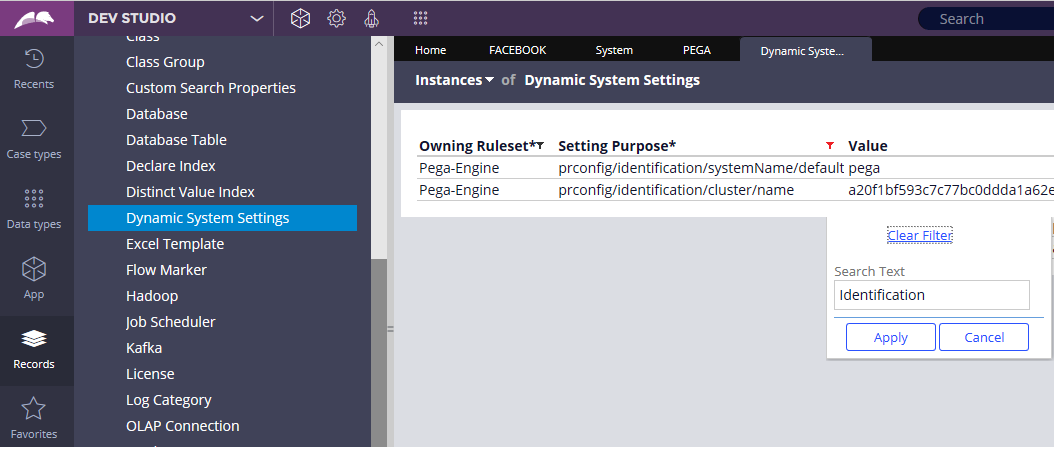
You see a rule name – prconfig/identification/SystemName/default. Open it and you will see the default system name as pega.
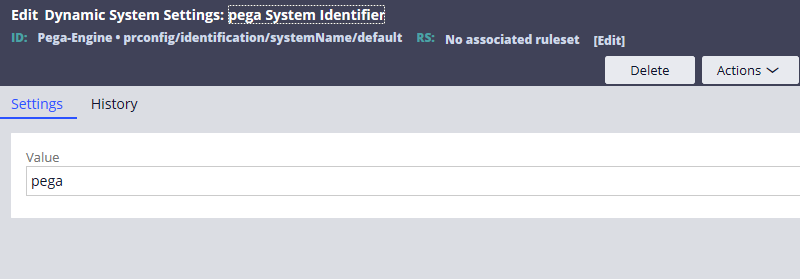
Now update the value to the new system name – facebook, save the rule.
Step 4: Now restart the server for the changes to be effective.
Step 5: Once restarted verify your current system name as facebook (earlier it was pega)
System -> General -> Systems, Nodes, Requestors
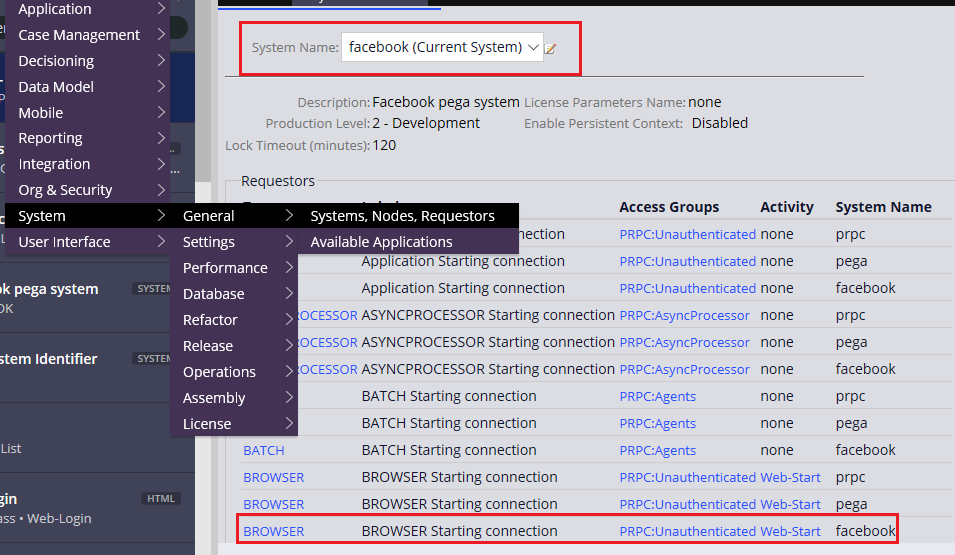
You see facebook as the current system and requestor types were automatically created for the facebook system.
Now if you launch the URL again, then a new browser requestor session corresponding to the current system – facebook will be created.
You can click and open the BROWSER requestor.
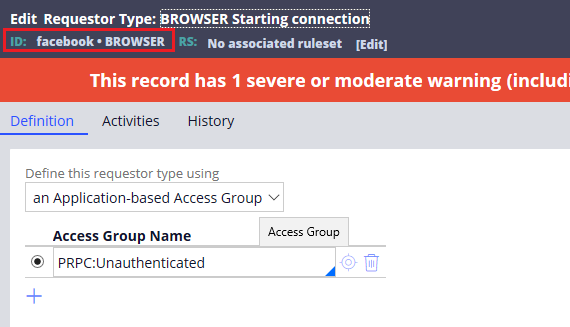
Now the pre-requisite is done.
What are the steps to customize the login screen?
Step 1: Create a new unauthenticated access group corresponding to your system.
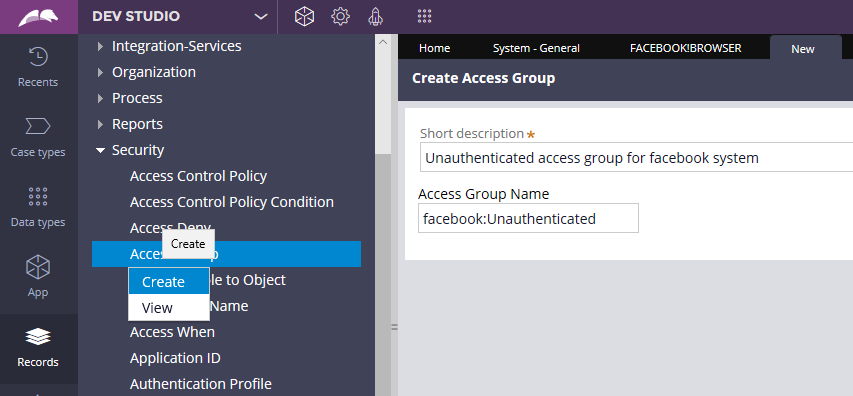
Configure the access group as shown below.
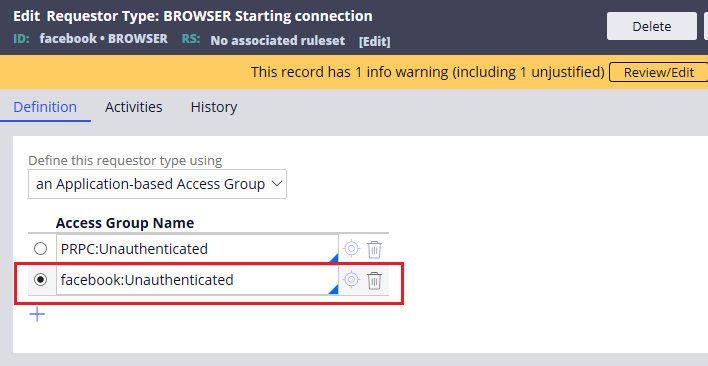
Step 2: Add the above access group to the facebook BROWSER requestor type and save the requestor type. Make sure you select it.
Step 3: Create a new unauthenticated ruleset – facebookUnauthenticated.
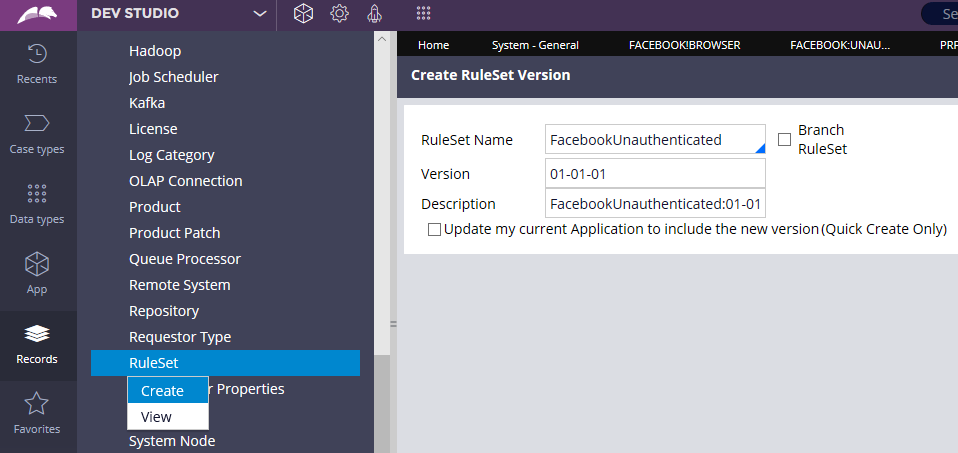
Save the rule.
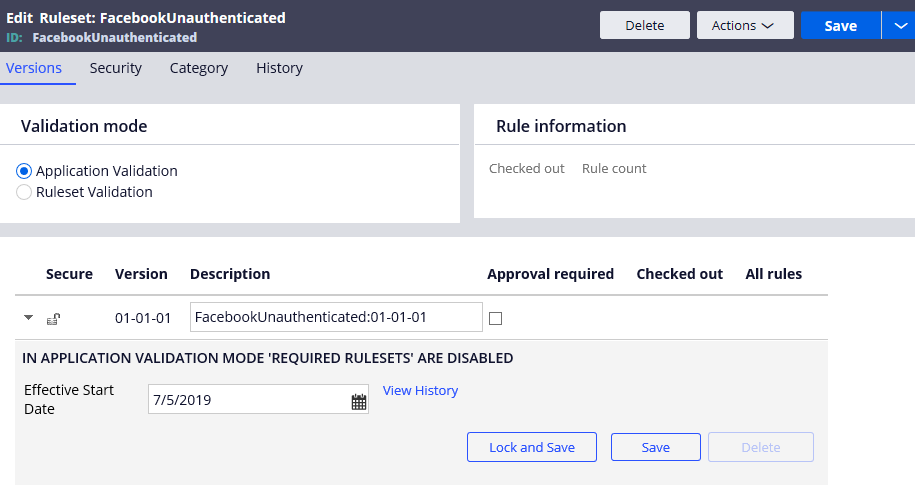
Step 4: Now include the unauthenticated ruleset as a production ruleset in the facebook:Unauthenticated access group advanced tab. Save the rule.
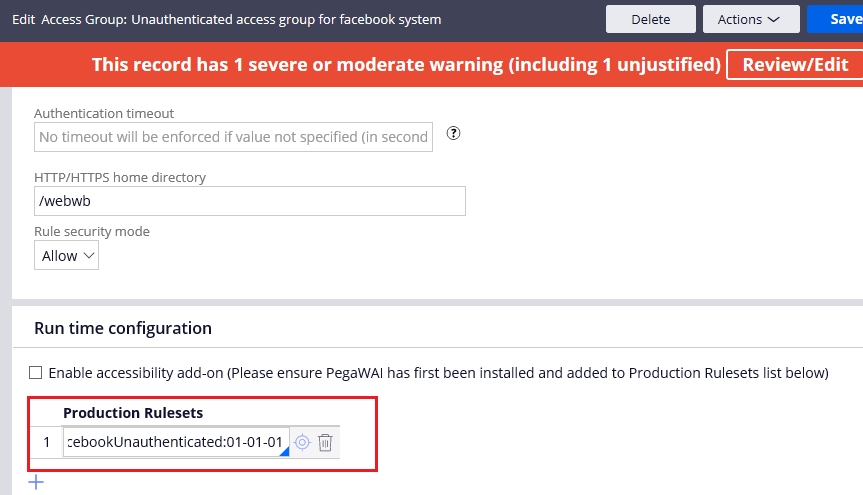
Note: Ignore the warning! This ruleset cannot be associated with any application.
We have successfully created the Unauthenticated ruleset. Now rules in this ruleset can be accessed by the Unauthenticated users using the browser requestor session.
Step 5: Web-Login, HTML rule is responsible for rendering the login page and its actions. Please explore the html and jsp tags on your own.
I am going to just change the background image of the login page.
The style attributes are grouped under a separate css text file rule py-login-screen.css.
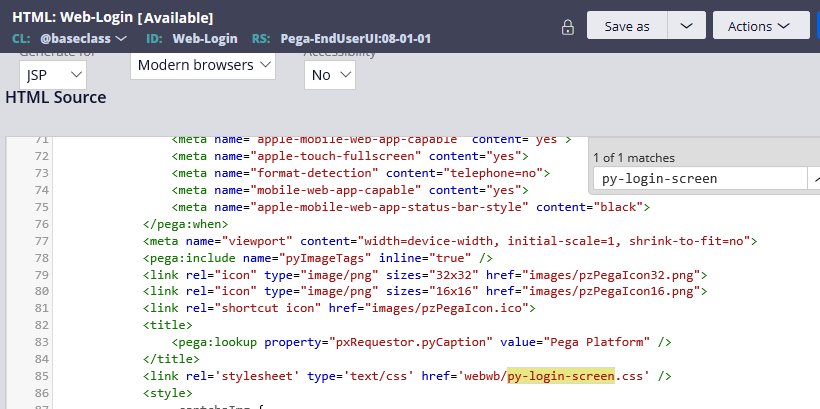
Step 6: Save as the text file – py-login-screen.css rule in the unauthenticated ruleset.
Update the css style for the background image as shown in the below picture.
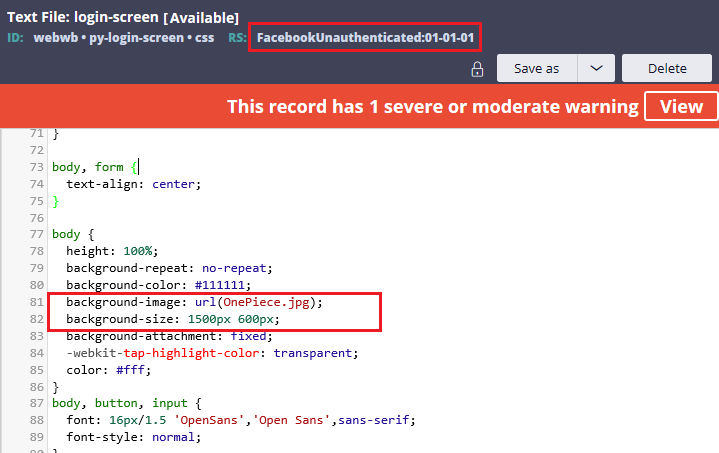
Note: To refer a image, use the format – url(<imagename.format>), you need to save the image in the directory webwb.
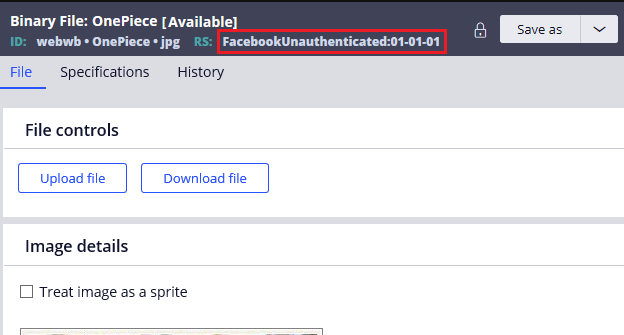
I already saved the image as a binary file rule in the unauthenticated ruleset.
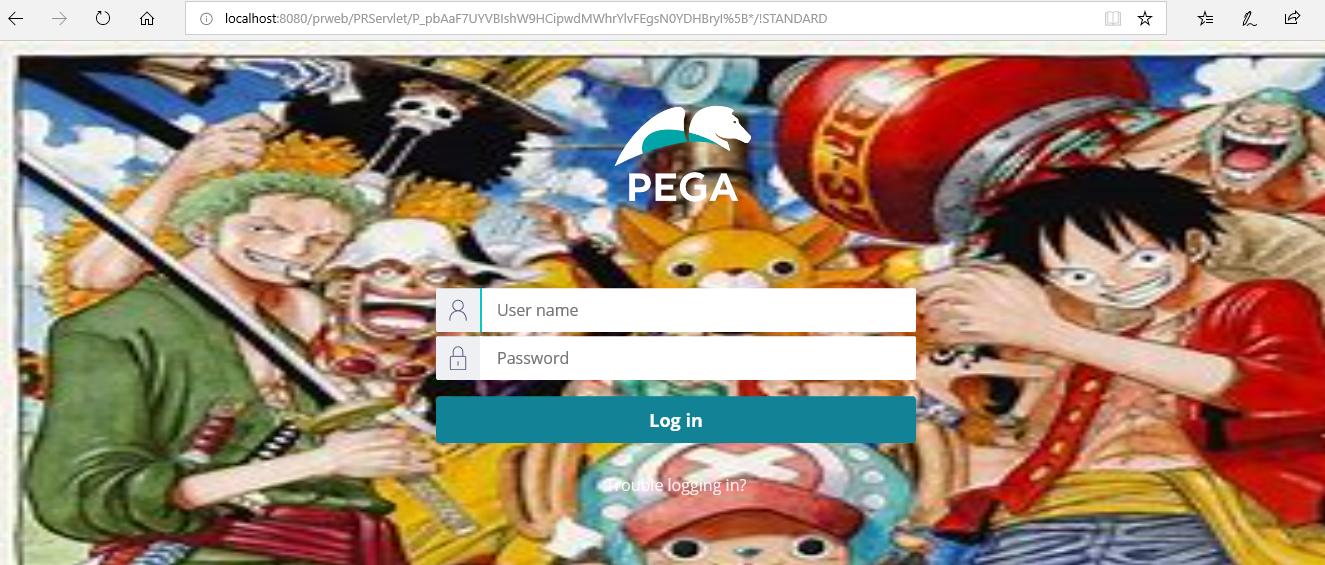
Time to test the One Piece Pega homepage! Launch the pega url again!
Now you know how to use the unauthenticated ruleset effectively and how to customize the login page. In the coming posts, you will see few more rules take their place in this unauthenticated ruleset.